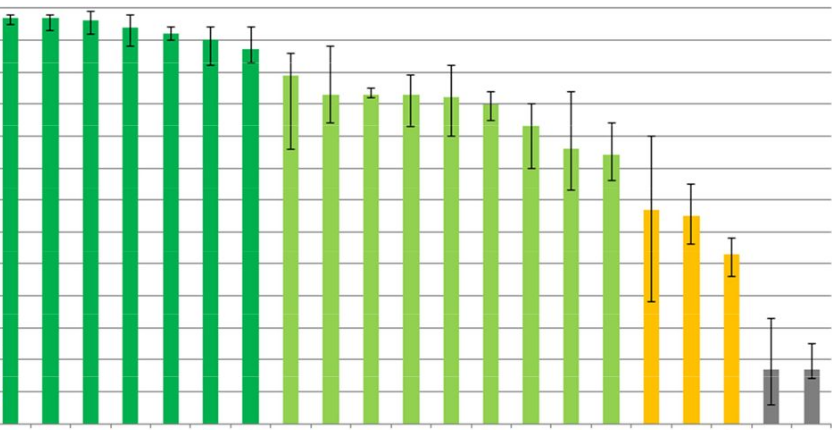
A good read about the status of Anti-Virus testing market. My take on this is test what you are buying. After all that is why products come mostly with a month worth of trial. Do take advantage of the trial and most importantly conduct your own...
The African continent isn’t immune to the onslaughts of cybercriminals. The Eastern region in particular has seen a rise in cyber enabled crimes in recent years targeting its infrastructure and telecom industry. Kenya has opened a Center...
I made a talk at the the 3rd Cyber Security Forum 2016 in Riyadh. In this talk I focused on the fact that security in most organisations is silo aproach. This is no longer helping as most of the IT systems we use today are fighting their corner...
World’s largest cyber-defence exercise underway with 26 nations & 550 leading computer security pros.
Follow this link ow.ly/4mVUV8
How I passed my CISSP Note. By no means am I implying this is the only way to study the CBK or prepare yourself to pass the CISSP exam. It does not mean you will or will not pass the exam by fallowing my style. We are all different and everyone has...
When we procure a system or software, we often leave the default settings as setup by the vendor. That might not always be good for security. One of the most important components of any systems security work is the development of a consistent...
FBI admin error leads to porn, drugs, malware and more as it loses control of website. You have to read to believe.
In late 2014 an attack came to the attention of the security world known as the POODLE attack. POODLE stands for Padding Oracle On Downgraded Legacy Encryption. The attack underscored the vulnerabilities introduced when legacy protocols with...