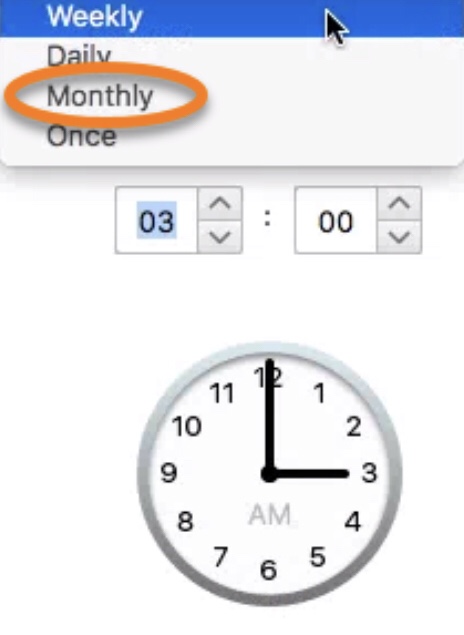
Lets look into the basics of schedule scan also known as on-demand scan (this includes right-click scan). In the days when endpoint relied on anti-virus alone, schedule scan played a critical role in complementing the real-time scan also known as on...
The general public are waking up to the reality that password alone is not a long term solution. More and more people are opting in for a more secure way to safeguard their digital life by way of enabling two factor authentication (2FA) -also known...
Bruce Schneier is a well known cryptographer, author and cyber security expert. Here is Bruce answering Reddit community’s questions in a “Ask Me Anything” style. If you ignore his book promotion mention, there are a lot of good...
The General Data Protection Regulation protects European (GDPR) citizens’ data. This forces organisations to ensure measures are in place to uphold the safeguard of this data if they are hosting, exchanging or transacting with it. The...
Here is an interesting research from Ruhr-Universität Bochum & New York University Abu Dhabi detailing attack vectors on LTE protocol -better know as 4G.
The first government owned organisation in the Middle East closed its data centers and moved its entire IT infrastructure to the cloud, ITP reports. This is largely to reduce cost but also improve security. “We are proud to be the first...
I am sure you’ve heard a lot about the EU’s General Data Protection Regulation by now. The wait is over and GDPR has arrived. It has far wider reach than people think. Review what it means and it’s reach here but here is what you...
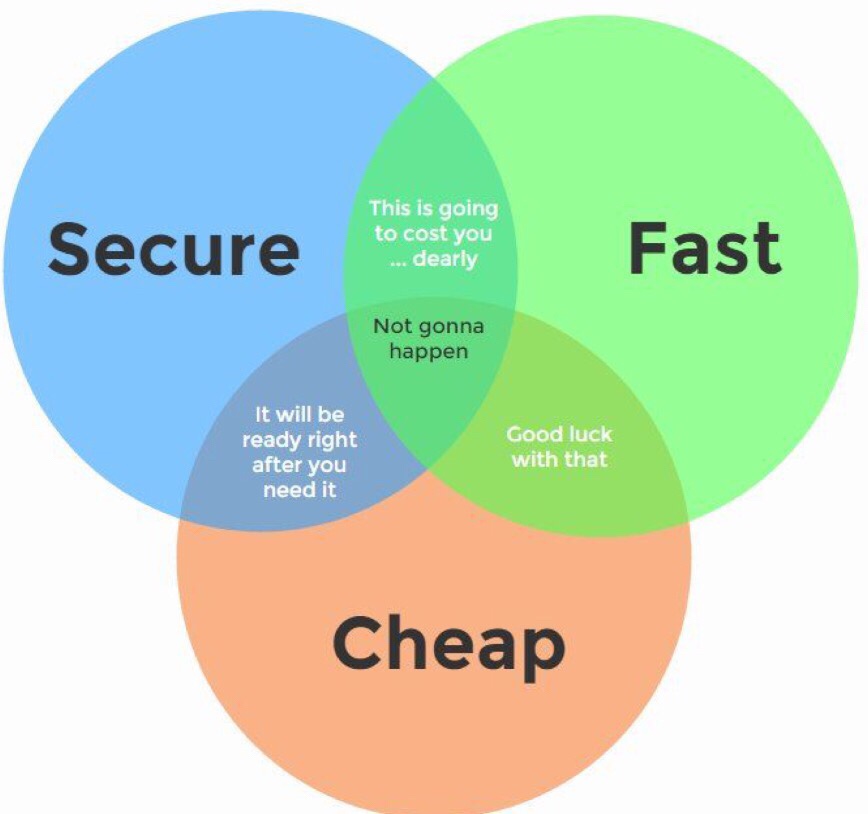
Cyber security is the act of having a safeguard or countermeasures in order to mitigate a potential risk. When I talk to clients who are looking at improving their security posture I often remind them that they need to strike a balance between...
Have I Been Pawned is a service whereby typing your email address you can check whether that same email appeared in a leaked or comprised database. The UK and the Australian governments are now using the service to keep an eye on their own domains...
Researchers have found numerous flaws in Advanced Micro Devices better known as AMD. The firm behind the findings is CTS-Labs. The attacks work on popular motherboards such as Tyan, ASUS, ASRock, Gigabyte, Biostar who all used AMD. The CPU...