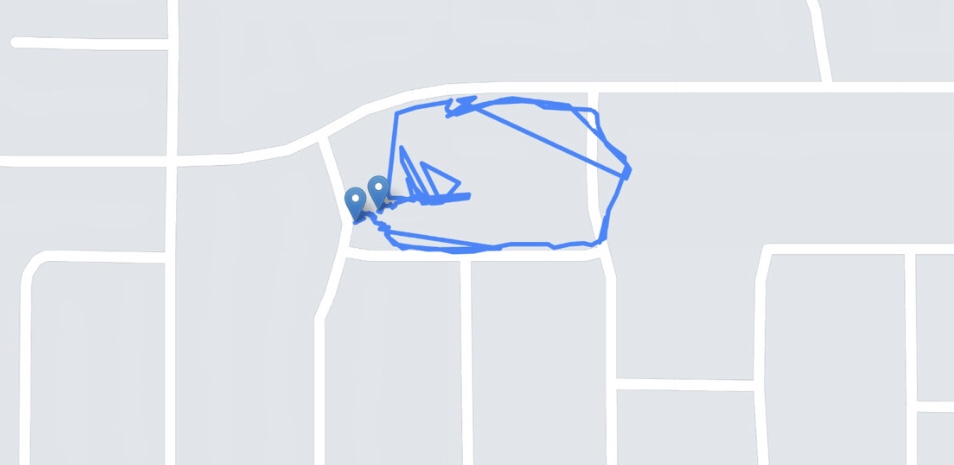
There is a good reason why we should limit location feature in our smart phones and portable devices. The US National Security Agency published a helpful reminder. However take the following into account; the “document may be useful to a wide range...
Here is a good presentation from SANS putting things into perspective. The slides are here .
Zoom has an actively exploited vulnerability. Zoom is a “remote conferencing services company headquartered in San Jose, California. It provides a remote conferencing service that combines video conferencing, online meetings, chat, and mobile...
Another go for encrypted file sharing. This time it is from Mozilla better known for Firefox, the open source browser. The service named Send thought not perfect allows you to share files 'safely'. In the word of Mozilla blog post "your stuff does...
Security researchers from the Switzerland discovered HP shipped some laptops with a keylogger. The code is part of the audio driver software which allows playback of audio sounds. Unfortunately this captures every keypress you make and saves it...
A look into why we choose the password we choose and what this reveals about us. A lot than you might think. If you ignore password managers – which combat linking the password to the individual by randomizing it, a password is more than...
On the 28 of March the US House of representative gave the green light to the Internet Service Providers to monetise your browsing habits. Obviously this is not a good news for most of people and angered the security community. This has forced...
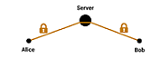
Encryption is in the news again. The UK Home Secretary expressed her frustration over encryption and in particular End To End encryption when it was revealed the man who carried out the terror attack at Westminster last used WhatsApp. ...
This is interesting but certainly not surprising seeing how much data we are willing to leave behind everwhere we go.
This is a good paper I came across thanks to Schneider’s blog: Enabling Trust by Consensus