This is a very serious leak as VPN (Virtual Private Network) username and passwords could undoubtedly allow the bad actors to access a network to perform all manner of activities including stealing date (data exfiltration), install hidden malware or...
Microsoft has released an out-of-band security update for a serious and actively used number of exploits on Microsoft Exchange. They named it Hafnium. The following versions of Exchange Server are affected: Exchange Server 2013 Exchange Server 2016...
Just before the turn of the year, Travelex, the foreign currency exchange service suspended their online services and took their systems offline after “a software virus was discovered”. They put out the following notice which is still...
Security is a jigsaw. It has a lot of pieces (network security, email security, endpoint security etc) but to have the perfect fit, you have to align them correctly. You cannot replace a piece with a different piece even if you have more than one...
For modern processing to optimise their data crunching, they do something called branch prediction. For example in a high level, if you have an IF statement and if x=1 you would do one thing and if x=0 would do another. What modern processors might...
The Meltdown and Spectre are serious vulnerabilities and have wide reaching impact. They affect nearly every computer and device running current processor. Big vendors are affected including Microsoft, Apple MacOS, Google Android, ChromeOS as...
DDE or Dynamic Data Exchange is a protocol that establishes how application interact and send messages to share data through shared memory. The bad guys unfortunately were leveraging a loophole to exploit this by using a booby-trapped document...
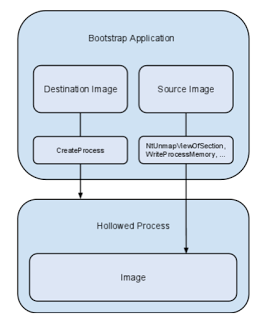
This is a good piece on process hollowing and atom bombing. If you ignore the marketing part of course.