The Cybersecurity and Infrastructure Security Agency (CISA) has released a companion Splunk-based dashboard that helps review post-compromise...
Latest from the blog
Microsoft has released an out-of-band security update for a serious and actively used number of exploits on Microsoft Exchange. They named it Hafnium...
Episode 1 – Series 1 – Anatomy Of A Phishing Attack
FireEye, a well known cyber security firm has been hacked. The company’s CEO Kevin Mandia has released a statement in a blog post on Tuesday...
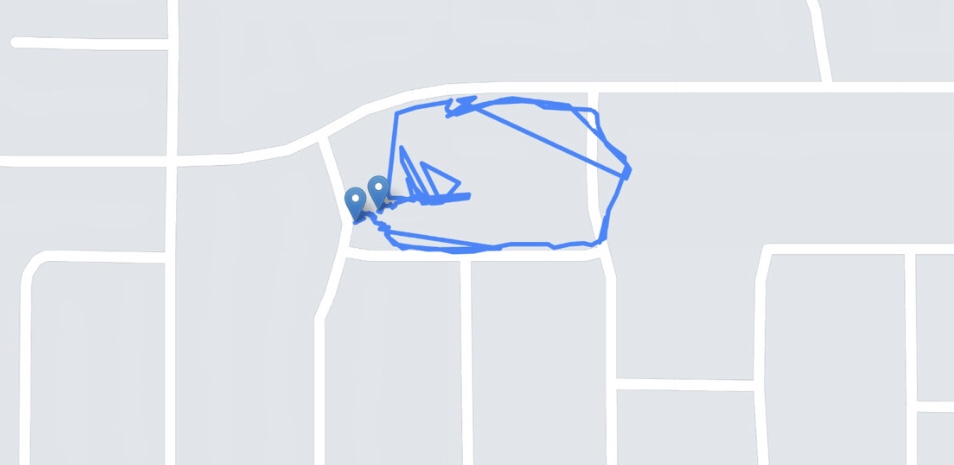
There is a good reason why we should limit location feature in our smart phones and portable devices. The US National Security Agency published a...
Here is a good presentation from SANS putting things into perspective. The slides are here .