Towards the end of November, a researcher from Alibaba discovered a fault (CVE-2021-44228) in a well known open-source logging library called Log4j. The researcher responsibly disclosed his finding to Log4j’s Apache Software Foundation.
An additional vulnerability (CVE-2021-45105) was also discovered in a patch released to fix the initial vulnerability. This was then followed with yet another remote code execution (CVE-2021-45046). It was all hands to the pump indeed.
Apache Software Foundation is collection of well-intended volunteer developers who keep maintain the software. It is an open-source software. It was clear that hackers could exploit this weakness to do dangerous cyberattacks across the globe by assuming responsibility for designated servers with remote-code execution. This danger has significant effect across all industry verticals.
With a deluge of hacks apparently up and coming, system admins are working round the clock to fix the loophole before the bad guys could get to it. Up to last week, the existence of this exploit was in secret until Apache publicly disclosed it.
Having said that, it is believe that Minecraft, the top-rated computer game platform, put up a blog entry telling the world that a form of the game had the Log4j vulnerability which could allow cyber criminals take over players; computer, and asked their users to urgently download a security update. The Log4j weakness was revealed. This put the whole cybersecurity community in frenzy.
What is Log4J exactly?
Log4J is a logging Library based on the Java language. It allows system admins as well as developers to keep an eye -in another word, create log entries for events on their servers. Logging is crucial as it is an important aspect of housekeeping. It also let the admins review for typical operation or abnormal behavior. In additional it is extremely important for forensicators.
The vulnerability, called Log4Shell, is caused by what programmers refer to as “incorrect input validation.” Normally, software would protect against data from untrusted users on the internet, but the hole allows them to pass, allowing data from untrusted outsiders to control the server’s operations.
That could entail everything from disclosing information online to automatically installing malware, according to Cisco Talos.
How bad is this vulnerability
Critically high. Compounded to that is the fact that Log4j, a Java library, can be found in a wide range of applications, including those from Google, Twitter, Microsoft, Amazon, IBM, Google, Cisco, Twitter, Steam, and even the US Cybersecurity and Infrastructure Security Agency. As a result, the flaw provides an opportunity for hackers to get access to millions of computer systems around the world, inflicting havoc.
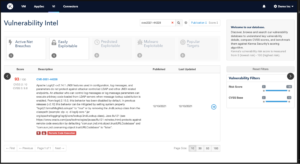
When I put this through Kenna Security, it assign a rare 93/100 score.
Image credit: Cisco.
The scoring system works as follows, take the highest score of the asset being score and multiply by the priority of the asset. Given this is more likely a server, it will certain be with the 8-10 priority score.
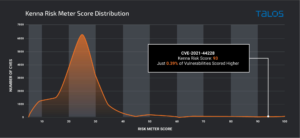
Image credit: Cisco Talos.
It appears to have started with a ransomware attack on Kronos, a labor management platform, which could cause payroll delays and which researchers believe is tied to Log4Shell. Other exploits include stealing processing resources to mine cryptocurrencies and legions of zombie botnets enlisting more devices to join their ranks. There are also indications that hackers have been scanning servers in large numbers in order to find vulnerable ones.
What has been done in response?
Companies must develop remedies for the flaw, ideally before hackers can use it in the wild. Many corporations, including Amazon, Microsoft, IBM, and Google, have stated that they have started to fix this and are continuing researching or working on fixing the problem as it evolves. However, a big headache—and the subject of much head-scratcher among cybersecurity experts—is that many firms may be unaware that they were built with Log4j, as applications are frequently designed with several components sourced from various sources. It’s a problem that a recent White House order aims to remedy by mandating companies selling software to the government to list all of the bits and pieces.
However, experts estimate that cleaning up the damage caused by the Log4j vulnerability will take months, if not years. This would need applying patched versions to all affected systems. It is fair to say that I t’s probable that some hackers who had previously infiltrated before the patch was applied, may set themselves a re-entry door (backdoor) that allowed them to access the servers even after they’d been patched.
Given the widespread use of Java and Log4j this is likely one of the most severe vulnerabilities on the Internet since both Heartbleed and ShellShock.
How to Mitigate the vulnerabilities
Implement one of the following mitigation techniques: Java 8 (or later) users should upgrade to release 2.16.0. Java 7 users should upgrade to release 2.12.2. Otherwise, in any release other than 2.16.0, you may remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Make sure you follow the step outlined here. You could check your assets are vulnerability as I did here although this can only be possible if you have a small number of machine. What you do need a is a scan for your entire estate.
Who is there to blame?
No one at all. Some are pointing fingers at Apache, alleging that the weakness should have been discovered and corrected in 2016, when researchers at the Black Hat cybersecurity conference demonstrated a way for exploiting a class of software that included Log4j.
However, the situation has brought attention to the fact that large swaths of modern software are built using open-source programs maintained by unpaid volunteers—who may be juggling a variety of other responsibilities—and has raised questions about what we can do to mitigate the disadvantages of this practice.
Additional material:
- Apache: The security updatefor log4j, alongside mitigation steps.
- Lunasec: Log4Shell: RCE 0-day exploit found in log4j 2, a popular Java logging package.
- Cygenta: Explaining Log4Shell in Simple Terms.
- Talos: Threat Advisory