Organizations are increasingly considering response capabilities within NDR solutions for dealing with threats detected through network traffic analytics tools, which are mostly focused on only detecting threats, and are largely focused around the core variations of known threats. NDR security solutions offer the added layers of network-level protection and threat prevention capabilities organizations mostly need today. This breed of technology is designed to continually monitor and analyze the company’s raw network traffic in order to create a baseline for the networks regular behavior. It is as if you turn your traffic into sensor that are always on.
NDR systems improve security capabilities through automated response to threats, enabling more effective communication between security teams and network operations teams, leading to better detection and mitigation. The network becomes a source of truth by flow information such as source and destination addresses, source and destination ports, the interfaces the traffic is flowing through, the IP protocol (TCP, UDP) or other telemetries.
Network detection and response (NDR) solutions continually monitor the business network, gathering all network traffic, applying behavior analytics, machine learning, and AI to detect cyber threats and anomalous behaviors, and taking appropriate actions to address those threats, either directly or through integration with other cybersecurity tools. NDR, also known as Network Traffic Analysis (NTA), monitors network traffic and builds a baseline of activities in the past weeks. They then use behavioral analytics and machine learning. Gartner has previously defined network traffic analysis (NTA) as an emerging category of security products that uses network communications as a main source of data to detect threats and investigate them inside the network. The event and alert are directly mapped to the Mitre.
NDR use cases are applied directly to the Kill Chain. (Cisco Network Analytics)
Threat Intelligence is used to assist in the identification of potential threats within the flow of network communications, and can be shared with other security solutions as part of a converged security architecture. If the threat intelligence is updated and available, it may assist the NDR solutions in finding known threats, or provide additional insight into the network abnormality detected, to enable it to be classified as risky. Flow data can help identify unauthorized traffic across the network and take advantage of resources and network performance, but can be lacking in the rich details and context needed to dive deeper into cyber security issues.
Use an enabled NDR solution to discover patterns and detect anomalies in your network traffic, which allows you to identify suspect or malicious traffic. NDR platforms leverage advanced machine learning technologies to profile network activity across all entities and identify abnormal attacking behaviors, rather than relying on third-party systems, which cannot accurately baseline activities over time or pinpoint hidden threats blending into legitimate activities. NDR products monitor East-West traffic, or communications inside the network itself, and apply advanced behavior analytics such as cloud-scale machine learning, to quickly identify, investigate, and react to threats that might otherwise stay under the radar.
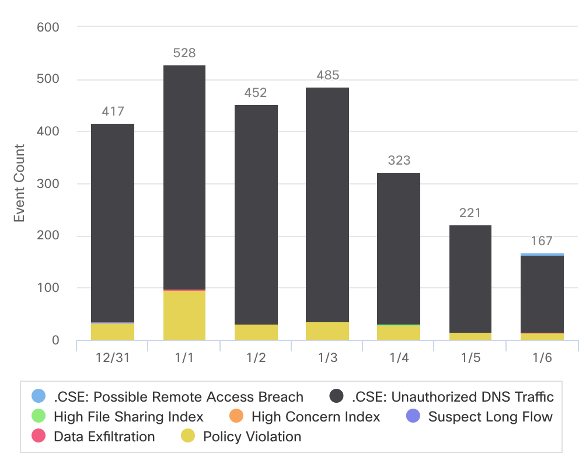
Alarm by type. (Cisco Network Analytics)
When NDR is integrated with other security solutions, like Network Access Control (NAC), log analytics tools (SIEM) and endpoint detection and response (EDR), the network blind spots can be closed, and a more robust cyber security strategy developed. NDR plays a key role in the wider threat detection and response strategy, working alongside other Security Operations Center (SOC) solutions, such as SIEM, Endpoint Detection and Response (EDR), and SOAR, to deliver a unified view of potential threats, using the Zero Trust approach. Whereas older siloed solutions such as anti-virus, firewalls, and endpoint detection and response (EDR) had a longstanding focus on threats on the network perimeter, NDRs focus is to monitor and respond to threats inside an organizations networks using AI (AI) and machine learning (ML) analytics.