A massive ransomware attack is under way and has hit major orgonisations. So far I am aware of the UK being hit particularly bad. It is a ransomware with the ability to propergate with the vixtim’s help and this means once a machines is infected the attack does not stop there, it moves laterally by scanning the adjacent network and start infecting neighboring devices. The infection does occurs without requiring the victim opening an email or clicking on links.
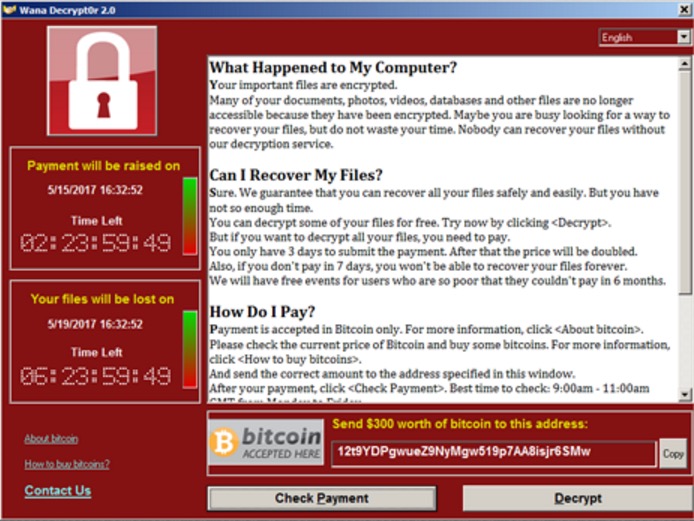
The victims of the WannaCry will see this note requesting the virtual Bitcoin equivalent of $300.
In addition it also carries out an outbound scan on machines on the Internet with port 445 open.
The entry point is a vulnerability (Eternalblue) in Windows Microsoft systesm. Eternalblue is a vulnerability reported back in April by the so called Shadow Brokers as par of their datadump allegedly stolen from the NSA. This would be one of the early instance of one the state sponsored hacking tools being used ruthlesly as part of money generating malware attack -ransomeware in this instance. This has already hit tens of thousands of machines worldwide. In particular what has attracted everyone’s attention is the type of machines that have been hit. In the UK one of the major organisations which have fallen victim is the National Health Services (NHS). This include systems monitoring critical patience care. So it is a pretty nasty attack. Spain’s Telefonica is another organisation badly hit. The tool used takes advantage of now patched existing vulnerability in Microsoft Windows Server Message Block version 1 (SMBv1). In the context of Windows SMB is a network file sharing protocol developped back in the era of Windows 2000. It uses different layers of the operating system layer such as NETBIOS transport or TCP/IP and allow you to connect to another machine to share data. SMB is on version 3.0 at the time of this writing. The problem is that multiple Windows support different version of this protocol. So for example in Windows 10 you can enable version 1 of the protocol. SMB has a built-in more than one layer of security such as user level and share level security. The authentication i.e. password that go between these differ layers are encrypted using CR (Challend-Response) type authentication method. This depends on the version of the protocol and how this is handled. So SMBv1 of the protrocol obviousely has this vulnerability used by the leaked tool and this is exploited if it is enabled. It is worth mentioning that SMBv1 is enabled by default in some of the Windows operating systems.
You really need to go ahead and disable SMBv1 and ensure you applied Microsoft’s MS17-010 (critical). You should at least block inbound SMB traffic or you can easily be a victim of this attack. Follow this Microsoft Knowledgebase article on how to disable SMBv1, SMBv2, and SMBv3 in Windows.
This is a wake up call to make a greater effort to make the basics of security right and how important it is to do that.
The lesson learned is patch early, patch often and always have a well tested backup.







